Java SAML Single Sign On (SSO) Connector | Java SSO
miniOrange Java SAML Single Sign On (SSO) Connector acts as a SAML Service Provider which can be configured to establish the trust between the SSO connector and a SAML capable Identity Provider to securely authenticate the users into your application. The SSO connector uses the SAML protocol for exchanging authentication and authorization data with the Identity Provider.
Key Features
Single Sign On
Easy and seamless access to all resources. Java Single Sign-On (SSO) via any existing SAML 2.0 Identity Provider
Protect Your Complete Site
You can restrict your site to only logged in users by redirecting the users to your IdP if logged in session is not found
Single Logout
Allows a user to logout from all server sessions established via SAML SSO by initiating the logout process once.
Attribute Mapping
Offers you to map the attributes from your IdP to your Java application
Role Mapping
Map your Identity Provider roles to your Java application and restrict resources to specific roles
Multiple IDP's Supported
Support SSO with multiple SAML Identity Providers
Custom Certificate
Add your own custom X.509 Certificate for sending signed Request and verification of signed Response.
Page Restriction
Page based restrictions over users based on their roles and whether they are logged in or not.
Auto-sync IdP Configuration from metadata
Keep your IDP SAML Configuration and Certificates updated and in sync
Secure Two Factor Authentication
Provides support for two factor authentication during login via a range of methods (15+ authentication methods), including text message, hardware tokens and many more
Federation Support
Allows users to Single Sign On into the site via their institution that is affiliated with InCommon Federation
Plans For Everyone
-
FREE
$ 0 - DOWNLOAD NOW
- See the Free Plugin features list below
- Unlimited Authentications
- Configurable SP Base URL
- Custom Application URL
- Add Login link in your application
- Attribute mapping(Only NameID is allowed)
- -
- -
- -
- -
- -
- Support
-
PREMIUM
$ 449* - Upgrade Now
- See the Premium Plugin features list below
- Unlimited Authentications
- Signed Request
- Signed Assertion and Response
- Configurable SAML request binding type
- Custom Attribute mapping
- SAML Single Logout
- Force Authentication
- Custom Application URL
- Configurable SP Base URL
- Add Login link in your application
- Support
Steps to Configure the Java SAML Single Sign On (SSO) Connector
Step 1: Download and Setup the SSO connector in your application.
- Download miniOrange Java SAML Single Sign On (SSO) Connector from here.
- Include the downloaded jar file in the application.
- Copy the jar file and paste it in WEB-INF/lib folder of your project.
- Copy the following code and paste it in web.xml file of your project.
<servlet> <servlet-name>SSOServlet</servlet-name> <display-name>SSOServlet</display-name> <description></description> <servlet-class>com.miniorange.app.servlets.SSOServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>SSOServlet</servlet-name> <url-pattern>/sso</url-pattern> </servlet-mapping> - Access SSO connector from your browser with URL https://<your-domain>/<application-name>/sso
- Register into SSO connector by providing a valid email address and password.
- After registration, log in to the dashboard using the credentials you provided during registration.
Step 2: Configure the SSO connector using your Identity Provider details.
- You can configure the SP Base URL or leave this option as it is.
- You need to provide these SP Entity ID and ACS URL values while configuring your Identity Provider.
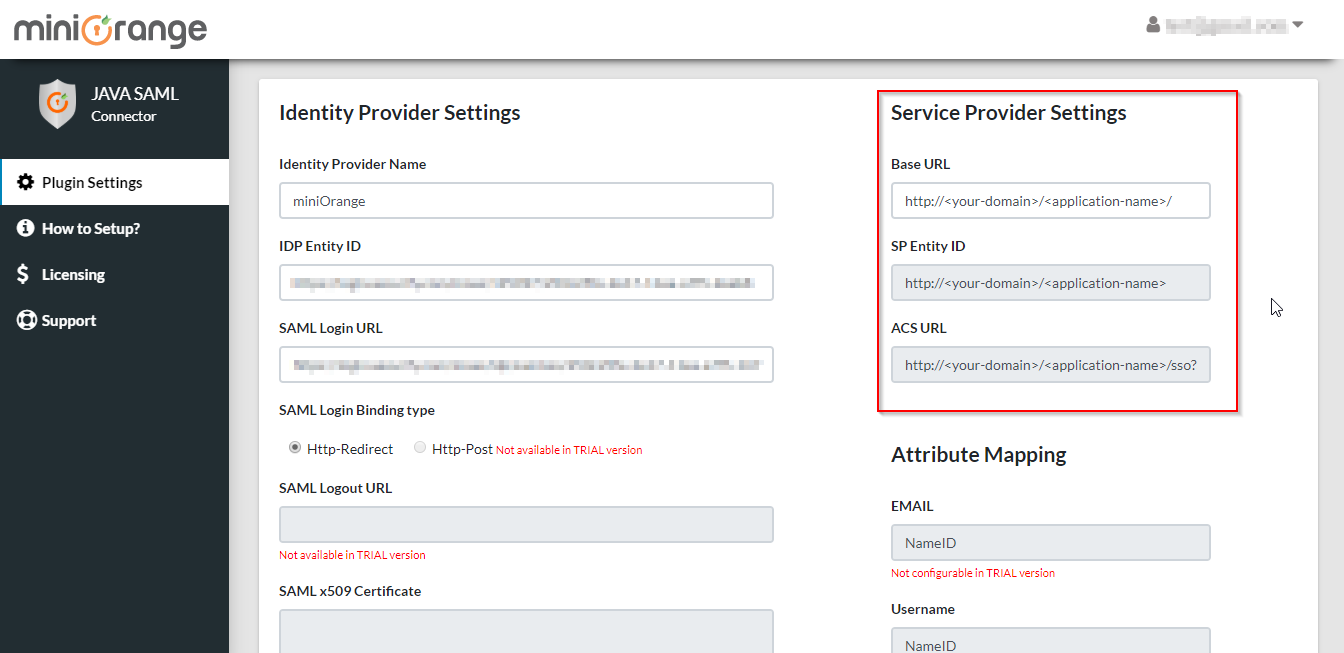
- Use your Identity Provider details to configure the SSO Connector.
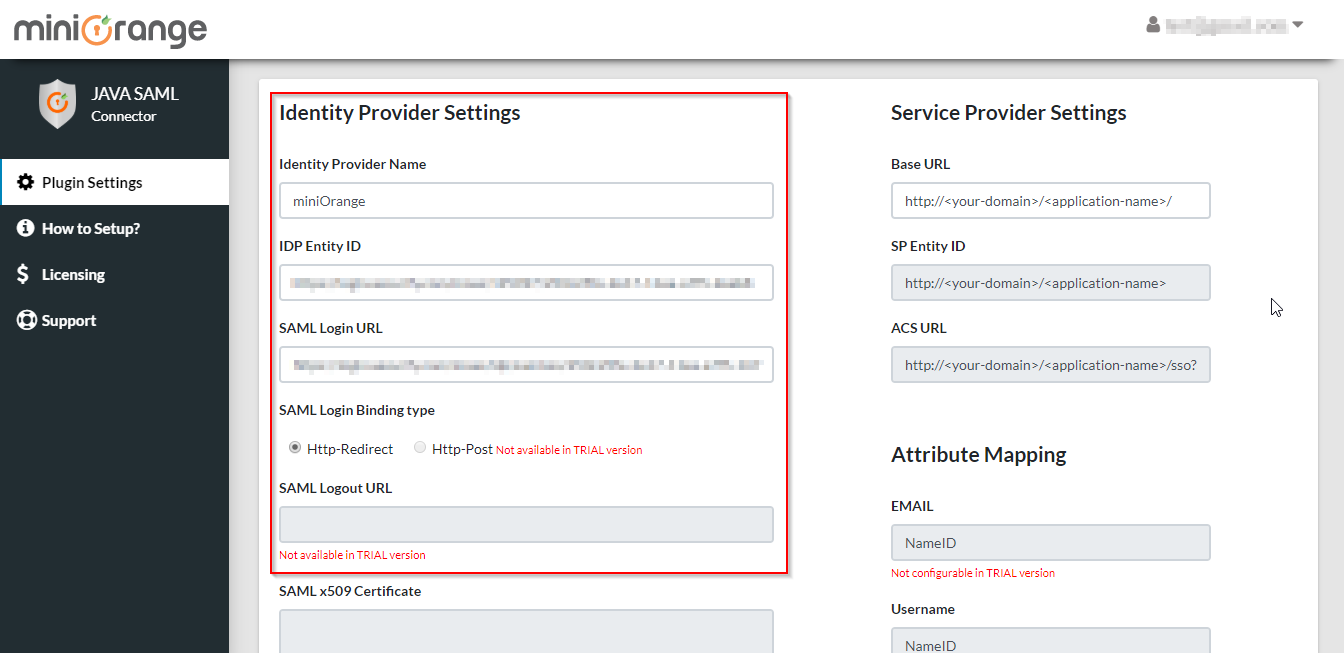
- Click on the Save button to save your settings.
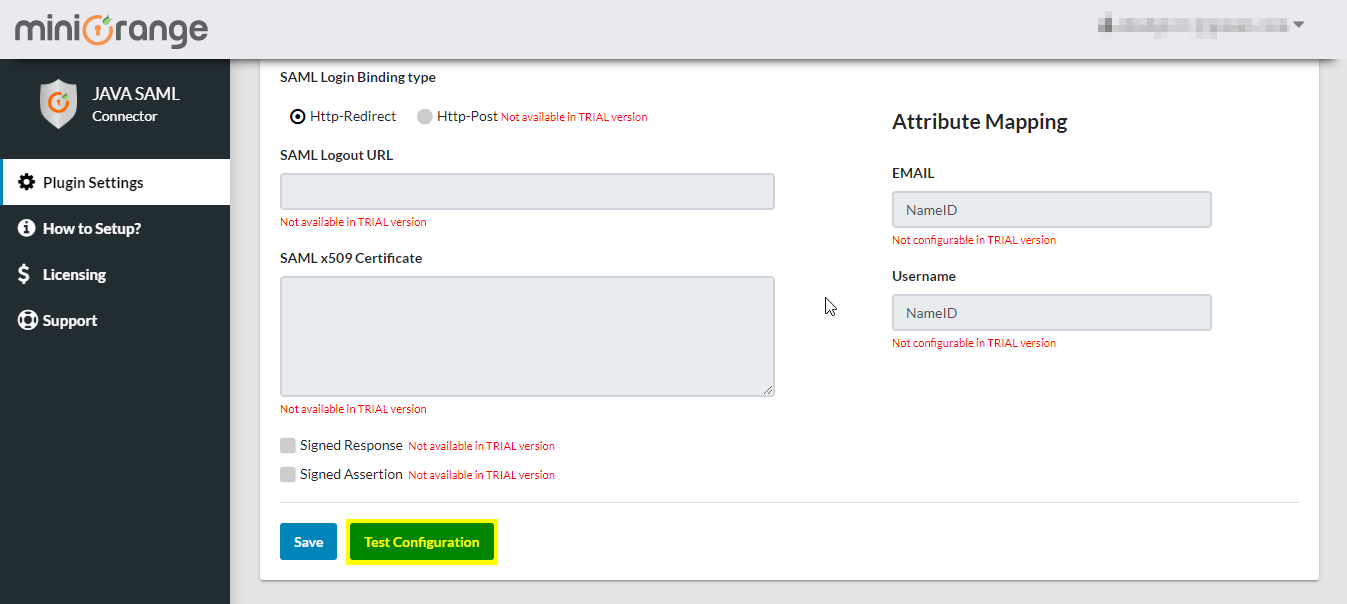
Step 3: Test the Configuration
- You can test if the SSO Connector is configured properly or not by clicking on the Test Configuration button.
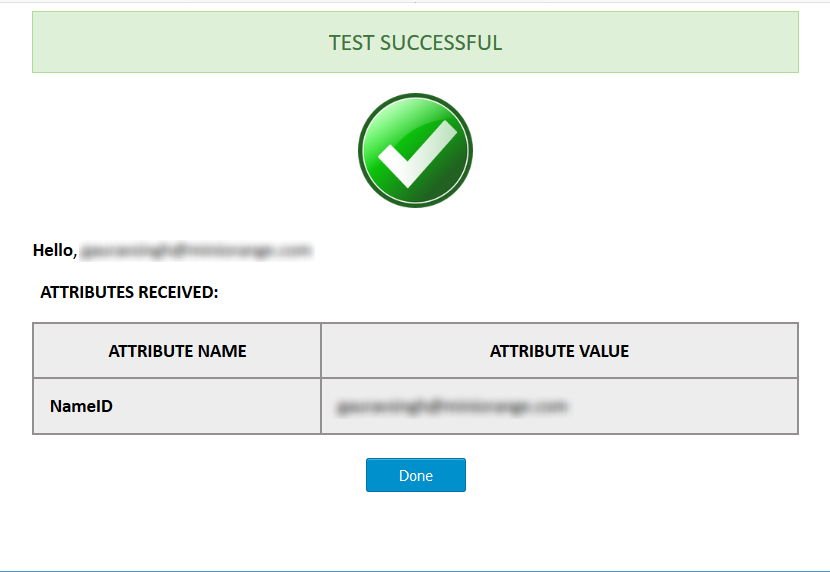
- You should see a Test Successful screen as shown below along with the user's attribute values.
Step 4: Setup the SSO connector to work with your Application
Once the SSO test is successful, you can provide the Redirect Endpoint, to where the users will be redirected after logging in.- To do so, click on the How to Setup? menu in SSO connector.
- Scroll down to find an option called Redirect Endpoint and provide the URL.
NOTE: The domain of the URL and the domain where you have setup the miniOrange Java Single Sign On (SSO) Connector should be same. - On this Redirect Endpoint you need to read the user attributes from the session variable that is sent by SSO connector and use that to login user into your application.
- You can use the following code snippet in your redirect endpoint to retrieve the attributes from the session variable.
The variable email will contain the received user attribute.HttpSession session = request.getSession(false); String email = (String)session.getAttribute("email"); - Now that the SSO Connector is configured, you're ready to use it in your application.
Use the following URL as a link in your application from where you want to perform SSO:
http://<your-domain>/<application-name>/sso?action=loginOR
You can use the following URL if you want to redirect user to a specific page after the SSO:
http://<your-domain>/<application-name>/sso?action=login&redirectto=<redirect-url>For Example, you can use it as:
<a href="http://<your-domain>/<application-name>/sso?action=login&redirectto=/<application-name>/dashboard">Log in</a>Your users will be able to SSO in your application by clicking on the Log in link
We can connect with any External IDP/Directory
Our Java Single Sign On (SSO) Connector provides user authentication from external directories like ADFS, Microsoft Active Directory, Azure AD, OpenLDAP, Google, AWS Cognito etc. It also provides user authentication with other IDPs like Shibboleth, PING, Okta, OneLogin, KeyCloak, Salesforce, SimpleSAMLphp, OpenAM, miniOrange, Centrify, RSA, IBM, Oracle, Bitium, WSO2, NetIQ and all SAML 2.0 capable Identity Providers
How to Setup Java SAML Connector?
Our SSO Connector works with any Java Framework
Our Java Single Sign On (SSO) Connector provides user authentication with any Java Framework like Spring Boot, Wicket, Struts, Tapestry, JSF, Hibernate, Blade, JHipster, Play, Spark, etc
Can't find your IDP ? Contact us on [email protected]. We'll help you set it up in no time.














